Traditional terminal programs have no graphical interface of their own. You can use them in a window inside a graphical user interface like Microsoft Windows, the X Window System, or Mac OS X, but there are no menus or icons.
There are some useful graphical versions of the SSH program for windowing systems which add extra functions like letting you store frequently-used addresses, usernames, and passwords. In these cases, it is generally A Bad Idea to store the passwords, as anyone who can use your computer would then also be able to log in to your remote sites.
SSH comes with all Unix-based systems by default (Linux,
Apple Mac, Sun, HP, IBM, etc). To connect, open a terminal
window and type
ssh username@hostname
(substituting the login username and hostname of your
account where shown, eg ssh ontology@www.ucc.ie).
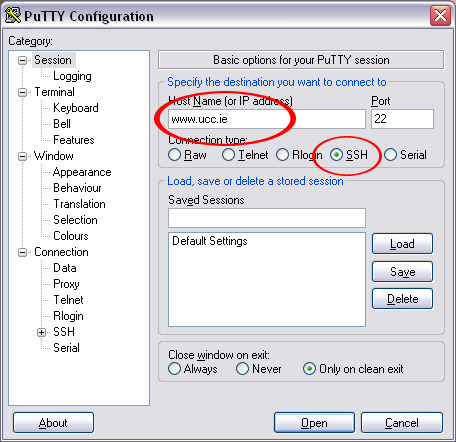
Windows users should download and install Simon Tatham's puTTY program from his web site at http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html, which provides an SSH window. Download or run the program called putty.exe.
You enter the hostname in the box provided, make sure it is set to use port 22 and SSH, and click on .
The very first time you connect to the server with SSH from a computer where you haven't done this before, it may ask if you wish to accept the public security key (this may be displayed in a separate pop-up window): answer by clicking or by typing yes and pressing Enter.
 Terminal Commands
Terminal CommandsThe authenticity of host 'www.ucc.ie (143.239.1.112)' can't be established. RSA key fingerprint is fc:10:cc:1e:54:53:f3:03:46:58:6c:0f:32:e3:5f:79. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'www.ucc.ie' (RSA) to the list of known hosts. login as: ontology ontology@www.ucc.ie's password:
SSH will then ask for your password: type in your password and press Enter. Once you are logged in, it's just a normal terminal.
The password will not be displayed, not even as a row of dots. Make sure you type it correctly!
On subsequent occasions you will just be asked for your username and password.
Passwords expire every 90 days on UCC servers. If you cannot log in, it's probably because your password has expired. To have your password reset, email the webmaster.
If you log in a few days after expiry, most systems will immediately ask you to set a new password. Make one up and type it in when asked (it asks you to repeat it, for safety). Remember that passwords do not display anything at all while being typed.
To change your password at any other time, type the command passwd . The system will ask first for your existing password. Then make up a new password and type it in when asked (it asks you to repeat it, for safety). Remember that passwords do not display anything at all while being typed.
 Terminal Commands
Terminal Commands$ passwd Changing password for user ontology. Changing password for ontology (current) UNIX password: Enter new UNIX password: Retype new UNIX password: passwd: password changed $
On systems where passwords are stored in Microsoft Active Directory, it will ask for your Kerberos 5 password instead. Changing your password here will also change your Microsoft Windows logon and email password (they are all the same thing).
 Keep up to date with our RSS newsfeed Keep up to date with our RSS newsfeed |
, Electronic Publishing Unit • 2009-04-22 • (other) |